Worried about online tracking and surveillance? This ultimate guide reveals how to achieve truly anonymous web browsing. We explore three powerful tools: VPNs for enhanced privacy, Tor for anonymized network routing, and Tails for a completely secure operating system. Learn how to combine these for maximum protection and reclaim your digital anonymity. Discover the best strategies to safeguard your data and browse the web with confidence.
Methods: Using a VPN (Virtual Private Network)
Step-by-Step Instructions
-
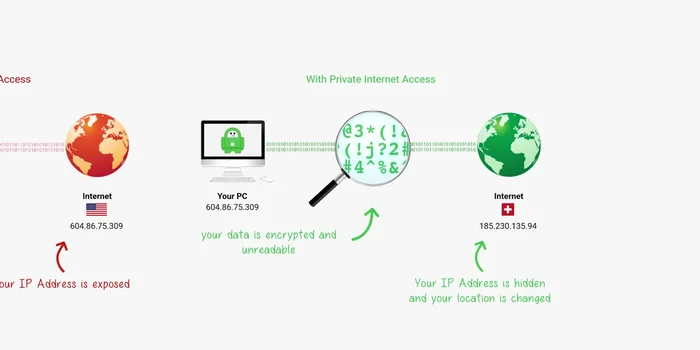
VPN Encryption and Transmission
- Your data is encrypted and sent through the VPN's server network before reaching its destination.

VPN Encryption and Transmission -
VPN Decryption and Destination Masking
- The data is decrypted at the exit point, making it appear as if it originated from that location, not your computer.

VPN Decryption and Destination Masking
Tips
- A VPN secures your data from your ISP and circumvents firewalls, but your data is still visible once it leaves the VPN network.
Methods: Utilizing the Onion Router (Tor)
Step-by-Step Instructions
-
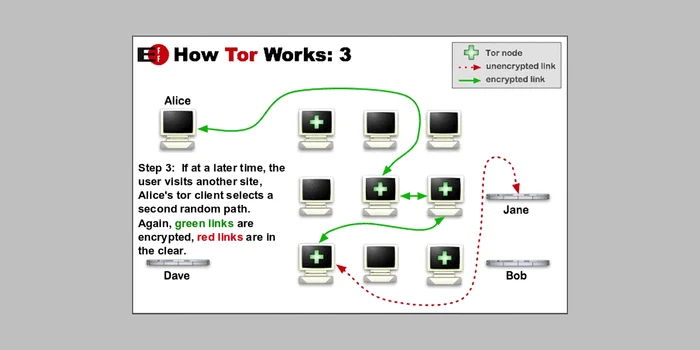
Using Tor for Anonymized Browsing
- Tor anonymizes data by using layers of encryption and sending it through multiple nodes.
- Each node peels back a layer of encryption, making it difficult to trace your online activity.


Using Tor for Anonymized Browsing
Tips
- Tor is imperfect; your traffic is vulnerable until it reaches the Tor network. Use a VPN to mask the initial jump.
Methods: Employing the Tails Operating System
Step-by-Step Instructions
-
Setting up Tails OS
- Tails OS is designed to forget everything once you shut down the system, making your browsing session untraceable.
- The entire OS is built around the Tor protocol, routing all internet traffic through the Tor network.

Setting up Tails OS
Tips
- Tails runs off RAM, so data is erased when the system is turned off. It can be launched on almost any computer with a USB port.
Common Mistakes to Avoid
1. Using a VPN Alone for Complete Anonymity
Reason: VPNs mask your IP address but don't encrypt your browsing activity within the VPN tunnel; your data could still be vulnerable to other threats like malware or tracking on websites.
Solution: Combine a VPN with Tor or another privacy-enhancing technology for stronger protection.
2. Relying on a Single Exit Node in Tor
Reason: Using the default Tor settings might lead to a potentially compromised exit node, exposing your browsing data.
Solution: Use bridges to connect to Tor and select a diverse set of exit nodes to increase anonymity.
3. Ignoring Metadata Leaks
Reason: Metadata such as time stamps, file sizes, and the length of your online sessions can still reveal information even if your content is encrypted.
Solution: Minimize metadata leaks by using privacy-focused operating systems like Tails and carefully managing your online activity.
FAQs
Is using a VPN, Tor, and Tails together overkill?
While using all three offers the strongest anonymity, it's not always necessary. A VPN alone offers good privacy for most users. Tor adds another layer of security, ideal for those concerned about surveillance or censorship. Tails provides the most robust protection, but is more complex to use and may be impractical for everyday browsing.
Are VPNs, Tor, and Tails completely anonymous?
No method is perfectly anonymous. While they significantly enhance your privacy, skilled adversaries with sufficient resources might still be able to trace your activity. Using these tools together minimizes the risk, but complete anonymity is an unattainable goal.